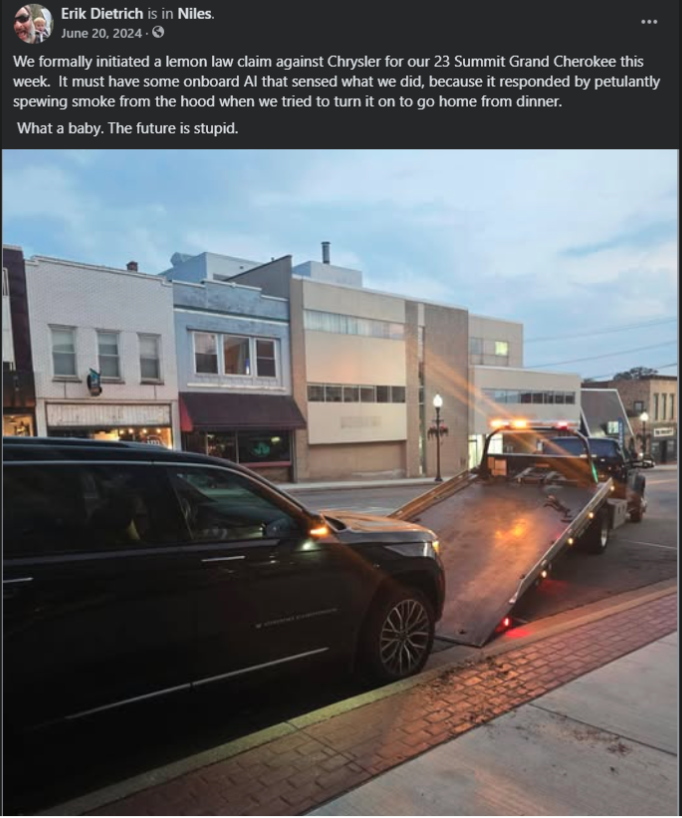
The Interesting Case of Flattening Mean Time to Mediocrity
I have a complex relationship with generative AI. On the one hand, I use it constantly and find it to be a godsend for some formerly laborious stuff. I’ll never visit another recipe site, comb through some dusty gadget troubleshooting site, or write boilerplate code by hand as long as I live. Read through terms…